A Model for Quantifiable Security ROI
In May of 2023, the City of Dallas, Texas, suffered a severe ransomwareWhat is Ransomware? Ransomware is a type of cyberattack in which the attacker infects a computer with malicious software that encrypts the victim's data. The computer usually becomes locked, presenting... More attack, rendering their networks inoperable. To their credit, they published a very detailed description of the event. While one may scoff at this, claiming that the report was mandatory, the City of Dallas should be commended for the candor provided in the report. Along with that, the information they share can benefit any organization that is seeking to create a quantifiable ROI matrix for a robust security program.
Too often, the security budget request presented to the senior executives includes many “what-if” scenarios that are easily dismissed by a weary and skeptical audience. Sometimes, the challenge is intentionally raised by stakeholders to test the proposal. After all, they have a vested interest in ensuring that the organization’s money is prudently allocated.
Introductory Facts
“Dallas is a municipal corporation of the State of Texas. As the third largest Texas municipality, the hub of the fourth largest metropolitan area of the United States, and the ninth largest city within the United States.”
The City of Dallas Ransomware Incident: May 2023
As with any large organization, this size makes it an attractive target for cybercrime. Along with that, it suffers some of the same administrative challenges as any large organization:
“The City of Dallas is comprised of over 40 different departments, multiple offices, and several boards that support the many different missions assigned to it. Each department, office, and board effectively manages its own activities in support of the assigned missions. This diversity of approaches provides diversity in approach but also introduces a certain lack of organizational cohesion.”
The City of Dallas Ransomware Incident: May 2023
Attack Execution
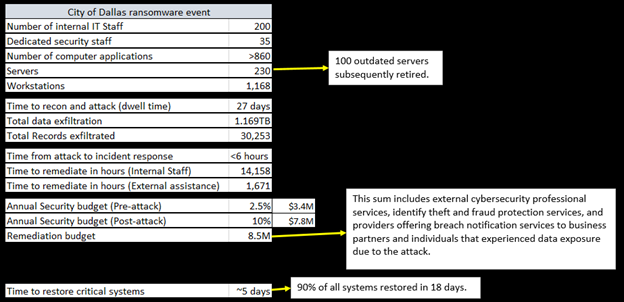
On May 3rd, 2023, criminals executed a full-scale ransomware attack against the City of Dallas’ network. The after-action analysis indicated that the attackers spent the prior 27 days performing reconnaissance, exfiltrating 1.169 Terabytes of information, including 30,253 records containing Personally Identifiable Information (PII)What is Personally Identifiable Information (PII)? Personally Identifiable Information (PII) is data that can be used to distinguish an individual’s identity. These can include identifiers that pinpoint the person exactly,... More. During this time, the attackers also planted beaconing software, remote access software, and the ransomware delivery mechanism.
The attack was determined to be the work of the “Royal hacker group” gaining initial entry via a domain service account:
“Royal’s initial access utilized the basic service domain service account, connecting to a server. Royal was then able to traverse the internal City infrastructure during the surveillance period using legitimate 3rd party remote management tools.”
The City of Dallas Ransomware Incident: May 2023
How can all of this seemingly dire information be used by anyone seeking approval for a cybersecurity budget? At first glance, it seems that the City of Dallas breach demonstrated a total failure, but a closer examination reveals an excellent case study. The incredible and beneficial lesson to learn is that the City’s network became compromised despite the fact that they had an incredibly robust and mature cybersecurity program.
Security Maturity
The after-action report mentions the use of enterprise-class firewalls, which is expected in any network, but it goes far beyond that. There were also 18 security initiatives in place in the organization, including, an Identity and Access ManagementWhat is Access Management? Typically delivered as part of an Identity and Access Management (IAM) solution, access management ensures that organizations allow users the necessary resources when needed, while restricting... More (IAMWhat is IAM? Identity and Access Management (IAM) is a framework of business processes, policies, and technologies to manage electronic or digital identities. IAM frameworks allow Information Technology (IT) managers to... More) platform, network behavior analysis, real-time threat detection, and a Security Operations Center (SOC). They already implemented a zero-trust architecture. The City also engaged in a Red Team exercise in February 2023, nearly two months prior to the initial compromise.
To add to that, these safeguards were not simply showpieces; the IT teams diligently held tabletop exercises and prepared formal risk assessments using Factor Analysis of Information Risk (FAIR) methodology, HIPAA Risk Assessments, and NIST 800-171 Data Confidentiality Assessments. This is further evidence of the type of security that would make many similar organizations envious.
Again, it would be easy to disdainfully dismiss these efforts, thinking that, with all this security, they got breached anyway. However, that is not a strategically defensible position, and many analogies are easily conjured up.
Analyzing the Numbers
The information shared in this report can help any security professional, as all the numbers are included that can be used to evaluate a security budget, as well as how to improve an already mature security practice.
The annual security budget prior to the attack was 2.5% of the total IT budget ($3.4M). The budget after the attack was elevated to 10% of the IT budget ($7.8M). It should be noted that we are not privy to the total IT budget prior to the attack, which was apparently reduced from the total 2023 budget, hence the disparity in the calculation between 2.5% equaling $3.4M and 10% only equaling $7.8M. The cost to remediate the event was separately budgeted at $8.5M, which, to date, has not been fully used. The final costs, as well as the forensic examination costs, will be provided at a later time.
Remediation information
The City had 230 servers, and 1,168 workstations. The remediation process revealed that, of the 230 servers, 100 of them were no longer necessary, and were subsequently retired. The time to restore critical systems was around 5 days, and a full 90% of the environment was in operation in 18 days. It would seem that even the City of Dallas discovered that they were suffering from server sprawl, which they remedied as part of the ransomware recovery.
A Cleaner View of All These Numbers
All of these numbers are more easily visualized here:
How You Can Use This Information
With the knowledge of all the sizes and specifications within the Dallas report, one could reasonably reduce or expand some of these numbers to fit a specific organization. For example, in very simplified terms, if the organization is only 10% as large as the City of Dallas, it could be presumed that the security team should equal, if not exceed 4 people. This reflects the proportional total of the 35 security professionals on the City’s staff. Similarly, if the security budget is only 10% as large as the $7.8 Million that the City of Dallas allocates, then the budget should, at least, meet the 10% level of $780,000.
Headcount and costs are easily manipulated. However, certain numbers cannot be as easily calculated. For instance, one cannot assume that the dwell time, or the time to remediate an attack can be reduced just because a company is smaller. In fact, many small companies may have as many servers as the City of Dallas, but that signals a different concern.
Too often, security events serve as little more than something to gawk at, and to be thankful of our own good fortune for not being victimized. While there are still many questions about how the attackers managed to compromise an organization with such a well-equipped security practice, it stands clear that if your security is proportionally less than theirs, then it is probably proportionally susceptible to compromise. In the case of the City of Dallas, there are not only valuable lessons to learn, but a model for our own planning.
If you enjoyed this article: A Model for Quantifiable Security ROI, please feel free to take a look at our back catalog here.




