What are Hashtags?
Using hashtags is basically like creating a library of content. Hashtags help group all relevant content together on social media based on keywords. It’s a feature that started at Google and then became extremely popular on X and Instagram before being adopted by Facebook, TikTok, LinkedIn, and many other social media platforms. But why do hashtags matter?
Why use hashtags in digital marketing?
Many users now use at least one hashtag when sharing any content on their social media accounts; by now, it’s almost second nature for most digital marketers.
There is no exact science on how many hashtags to use in a post, but two or three max seems to be the magic number. I’m not a huge fan of seeing tons of hashtags, especially in cybersecurity, as it looks like spam.
Popular hashtags are used to group content pieces of a particular type together to make searching for that information easier.
The key benefits include:
- The ability to jump on trending topics to be part of the conversation. e.g – #Ransomware.
- To target new followers who might be looking at relevant keywords. This can be fairly broad and target mainstream keywords such as #infosec and #cybersecurity, or you have the opportunity to go way more niche and focus on topics such as #NERC or #GDPR.
- Using trending hashtags as a way of targeting users on paid campaigns, particularly on X, which boosts digital marketingWhat is Digital Marketing? Digital marketing—or online marketing—is a catch-all term for promoting brands using the Internet and other forms of digital communication. Digital marketers use various marketing channels, such... More efforts. They are great for Facebook and Instagram posts too.
What are the most popular cybersecurity hashtags?
“What hashtags do I use?” It’s a question I often get asked by users who want to share content but who don’t have a ton of time. Instead of promoting “write, rinse and repeat,” I thought I’d share a few simple best practices for users to keep in mind.
1. Use keywords based on your subject.
If you’re talking about a ransomware attack on a company, it makes sense to focus on the type of attack – #ransomware – and the company name – #companyABC. You’ll find users who are interested in the subject (ransomware) and the users who have an interest in the company (#companyABC). It’s a great way to get in front of both audiences.
2. Don’t be too broad with general hashtags.
If you’re sharing infosec content and using things like #people or #food, unless it’s extremely powerful content that is relevant to a mass audience that extends beyond information security, your IT security-related tweets will go without meaningful engagement.
3. Hashtags aren’t case sensitive.
It doesn’t matter if you use #InfoSec, #infosec, #INFOSEC or #InFoSeC. Libraries aren’t case sensitive, so you’ll find everything you need in one place. However, as a user of X pointed out to me, there are a few issues to consider if hashtags are all lower-case.
Firstly, they can be hard for native speakers to read, but for non-native speakers, it can almost be impossible. Also, screen readers just plow through them with generally poor pronunciation which makes it hard for blind/visually impaired folk. If you capitalize the first letter of each new word, it will be more readable, translatable, and better pronounced in screen readers. It’s important to consider all users!
4. Look at what is trending!
If you’re attending an event, such as Infosecurity Europe, see what the official hashtag is. Then use some variants, e.g #infosec23, #infosec2023 and #InfoSecurity2023. It’s a great way to target folks who are going to the event but also anyone online that has an interest from afar.
5. Do your research.
Type the hashtag into the search bar and see what comes up. If no one is tweeting about it, then does it make sense to include it?
6. Make sure it’s relevant to your audience.
If you’re using different acronyms, make sure they fit with your audience. FIM might mean File Integrity Monitoring to you, but to most of the internet, it’s the World Governing Body for Motorcycle Sport. Don’t let your content get lost in all the noise of another subject!
7. Create a hashtag unique to your business/personal brand!
To help create a unique library for yourself or your employees, it’s a great idea to create a hashtag and ask employees/followers to use it. For this, it’s pretty easy to get creative and come up with something that everyone can get behind.
How to use hashtags in IT security?
When creating and placing hashtags, there are typically two approaches.
1. Add all hashtags at the end of the content.
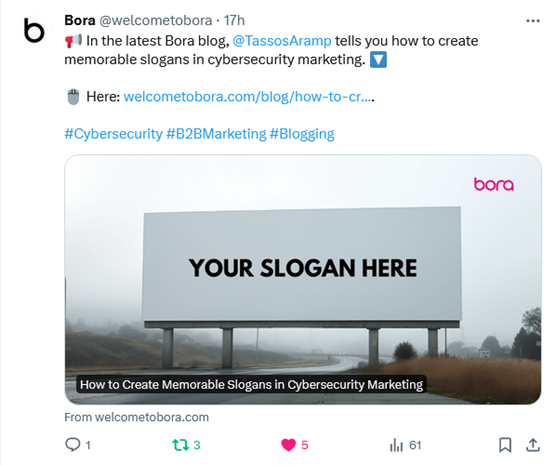
2. Include hashtags in the actual text.
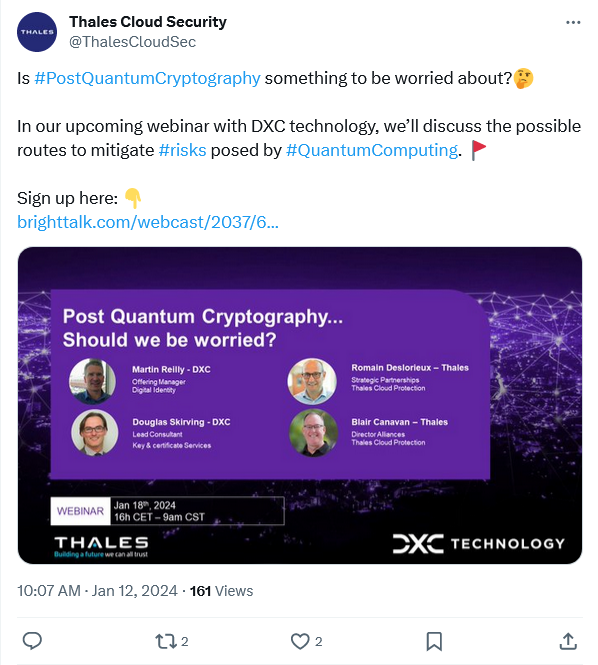
Personally, I prefer to place all hashtags at the end. I think it makes the text clearer and looks aesthetically pleasing. However, I’ve seen users try different approaches, and sometimes it might make sense to test both approaches. Bottom line, I don’t think it’s something to get hung-up on. Go with what works best for you and your audience.
There are many other things to consider when sharing content on social media. You might think about using shortlinks, tracking URLs, tagging relevant parties, tagging in photos, swapping titles for descriptive text and even how to format your content.
But that’s another blog post. To finish this off today, I’ve put together a list of IT security hashtags you might find useful. If you have any suggestions, feel free to get in touch!
#ITsecurity
#Cybersecurity
#Infosec
#DataProtection
#Spam
#AISecurity
#ThreatIntelligence
#DDoS
#Appsec
#Cybersecuritytraining
#Cyberthreat
#Cybersecuritytips
#Cybercrime
#Cyberattacks
#DigitalSecurity
#OSINT
#OPSEC
#Phishing
#RiskManagement
#DataBreach
#Passwords
#NetworkSecurity
#NetSec
#CybersecurityAwareness
#InformationSecurity
#DataPrivacy
#GDPR
#InfoSecurity
#Hacking
#CISO
#IoT
#CloudSecurity
#CloudComputing
#Microsoft
#Linux
#PatchTuesday
#DevOps
#DevSecOps
#Cloud
#ICS
#IndustrialCybersecurity
#IIoT
#IndustrialIoT
#SCADA
#OTsecurity
#NERC
#Malware
#Ransomware
#VulnerabilityManagement
#PatchManagement
#Vulnerabilities
#MalSpam
#NIST
#SecurityAwareness
#WomenInInformationSecurity
#DataSecurity
#CyberNews
#Hacker
#PCIDSS
#SecurityControls
#Pentesting
#WomenInCyber
#HTTPS
#AccessManagement
#Containers
#HIPAA
#Pentest
#Encryption
#Docker